
My dad sent this to me yesterday and I couldn’t stop laughing. Couldn’t tell you why for the life of me. Credit to Kate for the picture.


My dad sent this to me yesterday and I couldn’t stop laughing. Couldn’t tell you why for the life of me. Credit to Kate for the picture.
I find it ironic that my prototype solver (written in Python) is less buggy than my production solver (written in Java).
As promised, I’m here to report more of the White Rabbit happenings. At the request of my friends, I’ve omitted the actual QR codes and their decoded text for the benefit of the game. However, I will tell the events as they were.
Friday morning, we reconnected to the slowhiterabbit.org SSH account that we had previously deduced. The lovable ASCII rabbit appeared along with a PEM-encoded certificate, a set of GPS coordinates, and the following message:
Bring a camera, the view is beautiful.
The GPS coordinates were in the forest right behind campus, so after class, we all hiked to the coordinates given. Naturally, I brought my camera, and took a couple pictures on the way up.


When we got to the coordinates, we found a tree with the rabbit hanging from a branch and a QR code on the opposite side:

The QR code decoded to the private key for the certificate. We thought about what the certificate could be for, I decided to try going to https://slowhiterabbit.org/ , which requires a client certificate. After some command-line hackery, we created a browser-usable certificate file which allowed us into the website—a forum board. I registered, but just as the confirmation page appeared, my username began to delete itself, as if someone was hitting the backspace key. I freaked out. However, the username then replaced itself with the word “Alpha”. In the rabbit hole, just like in Project Mayhem, no one has names.
The quest will (presumably) continue next Friday…

There has been more White Rabbit activity involving GPS coordinates. Brandon and I are going to check it out soon.
After a week of midterms, studying, and stress, we were all excited to find a new White Rabbit message on the board by our classroom. In a strange twist, the rabbit message was not there before our lab, but had popped up an hour later. Freaky!
Anyway, so my previous post was just showing the new flier (in better resolution this time, since I grabbed my 6 megapixel Nikon D70s). The barcode was the same URL as before, but the QR code was (obviously) different. After running it through a QR code scanner, it returned this result:
-----BEGIN RSA PRIVATE KEY-----
MIIByAIBAAJhALWSG2+yBnYvjO5vQv/mI7WBm09YH9v6eUu4QTHUNQoOWqdFaZL0
Yekx7+iHgvA4m4uqlVp/LUMAZ10+mO2ufHzemL6M1KPqxr+sY7wWCsuZA6VyaR3n
YBnaaaBWbAZk0wIBIwJgKYB7TLr6KaR3+/wskkM7XK/o/DFmXiqfYcO3IVUTcANH
67gYIZbxzubXwB75W3qm0sT4GG4FPOcQjyIa9nH1wGabgEG646d9sowd2p93GL1N
f1rX6MRQYmbIAgQ1Ic3LAjEA71frKFmVheQC/2LPyYgLzdIrlJRgSQuxiivqi71s
9Kz8bf5oJntqv4nH/Oh6XP03AjEAwjTsx0RA0ql766aTLfPdhUuE2NjituJPSFt2
k970yq/UKkaQXREVq872mpuJNYNFAjA9i6LefW+XdSVXnRDcDQpZfy/HHtbuNjT3
pOSKVUfnJSr3tnKNjXM4kSTMAUQJSG0CMBClc2GJgeYryMsORyEyKO4rC2MLRqH2
JA2ELrw3rpUHwbp7E7A0qhYKbOiuPvX1TwIxANfA9NTZxf1K4+LoKInwQKWz2sRc
NS4CYsNpg3F0MPUXXH8VxlT+WvojZJ2OogoYIQ==
-----END RSA PRIVATE KEY-----
To most ordinary folks, this looks like unreadable garbage. However, to a programmer, this is an unreadable key. This discovery requires a bit of a lesson in basic cryptography, the study of obscuring—encrypting—data. It’s a wide field, but I’ll try to keep the background brief.
Back in the dawn of cryptography, people used Symmetric-key cryptography, which is what most people think of when they think of encrypting data. You type in a password and your data becomes junk until you type in the same password again. In cryptography circles, this password is called a key. This is all fine and good, but what if you want to give data to someone else? You could agree on a password with the other person and use that same password over and over (which is insecure), or you could keep changing passwords and having to tell that person in a secure manner what the new password is (which is inconvenient). Both of these seem like bad ideas, so what to do?
Then, in 1976, a couple guys discovered Public-key cryptography. In essence, one person can encrypt data with the other’s public key and the recipient can decode it only with their private key. Public keys can be distributed without fear, since only the private key can decrypt it.
The other useful property of this is using the private key for logging into other computers, via a useful protocol called SSH. The server can encrypt data using the user’s public key, and it can only be read by the user’s private key. It was at this point, my friends made an important discovery:
alice@slowhiterabbit.org is not an email address. It’s a login.
So lo and behold, we copied the private SSH key onto our computers and logged in to slowhiterabbit.org with the username Alice to find this:
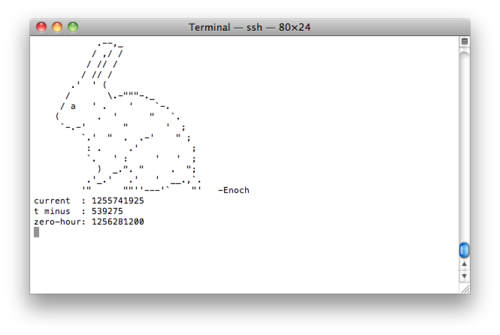
A countdown to 2009-10-23T00:00:00-0700. We think that this is when “Alice” will post her next message “through the looking glass” (so to speak) and not resort to fliers anymore.
It’s exciting, but the question is still: why is this happening?